The AI-SOC Revolution: Let’s Get Real
Attackers are using AI just as much as defenders now. They are sending smarter phishing emails, creating malware that changes shape, and moving quicker than ever.
As per Darktrace’s latest report, State of AI Cybersecurity 2025, industries are already facing AI-powered cyber threat:
Industries impacted by AI-powered cyber threats:
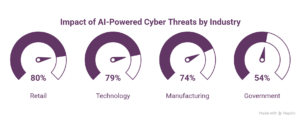
- Retail: 80%
- Technology: 79%
- Manufacturing: 74%
- Government: 54%
With AI-powered threats hitting sectors at scale, an AI-driven SOC is no longer optional, it’s urgent.
And the truth is, we often can’t even tell if an attack is AI-powered or not. That’s where AI in cybersecurity starts playing a serious role. So, what’s AI really doing in the SOC?
We need defenses that can keep up- fast, smart, and always learning. That’s exactly why AI-driven SOCs matter today. They don’t wait for alerts to pile up; they spot patterns, learn from every move, and act before things blow up.
When threats come at you in seconds, your SOC can’t be stuck in yesterday’s practices. It needs to think like an attacker but defend like a machine.
The Cognitive SOC: How AI Redefines Security Monitoring
An AI-SOC interprets data patterns, recognizes early indicators of compromise, and even guides analysts with decisions, not because it wants to replace them, but because it helps them stay sharp where it counts.
Companies are already using AI in SOC setups where AI-enhanced systems handle triage, recommend playbooks, or even fully execute responses under human oversight.
The Mess We Have Been Dealing With
The traditional SOC model has been faltering under its own weight. We all know the feeling when the alert volume becomes unbearable. Here’s what teams face daily:
- Alert Fatigue Crisis: Analysts spend hours clearing out false positives while the real threats play hide-and-seek.
- Monotonous Task Burden: Checking logs, matching patterns, dragging through SIEMs, rinse and repeat.
- No Decision Guidance: Even experienced analysts are often left to make critical decisions with half-baked data.
This is where AI in cybersecurity brings change.
Traditional SOC vs. AI-SOC: A Simple Breakdown
Let’s draw a line between traditional SOC and AI-powered SOC.
Traditional SOC | AI-Driven SOC |
Static rules and thresholds | Adaptive algorithms that evolve |
Manual triage | Automated alert prioritization |
Long incident cycles | Real-time or near-real-time resolution |
Human-centric for all steps | AI-augmented workflows with human eye |
AI doesn’t replace the analyst. It empowers them to stop acting like a glorified script-runner and start behaving like a real threat hunter.
Tech Under the Hood: AI Tools Enhancing the SOC
Let’s take a quick look at what’s powering this transformation:
- Deep Learning: Great at spotting anomalies in network traffic, malware behavior, and user activity. Tools like Darktrace use this to learn your digital DNA.
- Large Language Models (LLMs): These power contextual understanding. Whether it’s summarizing incident details or explaining technical anomalies, LLMs like GPT-based engines are stepping in as assistants.
- Chatbots and Co-pilots: Integrated into SOC platforms, these offer instant insights, suggest threat responses, and even draft initial reports.
- Automation Engines: Think of SOAR platforms like Palo Alto XSOAR or Splunk SOAR, built to run response playbooks without waiting for manual triggers.
Each of these technologies make AI in SOC real.
What Powers an AI-driven SOC
When you break it down, an AI-SOC is made of both threat-defense and analyst-support layers. Here’s what it looks like in real-world terms:
- Modern threats are AI-powered, so defending against them requires AI too: Cyber adversaries are now using AI too, for polymorphic phishing, dynamic ransomware, and invisible exfiltration tactics. You need AI to fight AI.
- AI tools act like proactive defenders: AI tools now predict attack vectors, identify weak links, and launch containment protocols autonomously.
- Faster Resolution: What used to take days can now be resolved in minutes. Not because humans are working faster, but because AI is cutting through the noise.
That’s what AI in cybersecurity brings to the table, clarity in chaos.
Meet Transilience AI: Not Just Another Tool
Our system, Transilience AI, does more than just catch threats. It does contextual threat correlation. That means if a suspicious file shows up on a device, it immediately checks if that file’s known elsewhere, what it’s doing, how it got there, and whether it matches past attack patterns.
Transilience AI:
- Filters out noise and only show what’s truly relevant.
- Learns from feedback, both analyst input and system behavior.
- Automates incident respond to actions like isolation, blocking, or alerting.
- Speeds up everything: detection, decision-making, and containment.
It’s like giving your SOC a hyper-intelligent sidekick.
How Transilience Works
- Filters out noise and only shows what’s truly relevant
- Transilience AI uses machine learning models trained to recognize patterns of benign vs. malicious behavior.
- Instead of flagging every login attempt, it filters out normal employee logins and highlights only the ones from unusual locations or at odd times.
- Learns from feedback, both analyst input and system behavior
- It applies reinforcement learning and feedback loops to adjust alert scoring and behavior based on past analyst actions.
- If analysts keep marking certain alerts as false positives, the system begins to deprioritize similar ones in future.
- Automates incident response actions like isolation, blocking, or alerting
- Uses pre-configured playbooks triggered by AI-driven threat scoring and detection confidence.
- When ransomware is detected on a device, Transilience instantly isolates the machine from the network and alerts the analyst.
- Speeds up everything: detection, decision-making, and containment
- Combines AI-driven threat modeling with real-time data processing and decision logic engines.
- Instead of taking 3 hours to confirm and respond to a phishing attack, it identifies, prioritizes, and blocks it within 3 minutes.
With Transilience AI, your SOC becomes sharper, quicker, and far more adaptive. It’s built to help teams cut through complexity and focus on what truly matters.
What Changes in the SOC Workflow?
The workflow inside an AI-powered SOC looks, and feels, different.
- Automated Triage: AI filters out noise and prioritizes real threats before analysts even log in, saving hours on alert reviews.
- Smart Alerts: Alerts now come packed with context, attack timelines, impacted assets, and LLM-generated summaries, ready for action.
- Faster Incident Response: AI suggests the next steps using prebuilt playbooks, reducing back-and-forth and manual investigation.
- Confidence Scores: Every action is backed by data, pattern matching, anomaly scores, and past case references to guide better decisions.
- Streamlined Workflow: No more jumping across tools. One interface, real-time collaboration, and AI-assist throughout.
Final Thoughts
For every SOC still stuck in manual mode, there’s another out there using AI to reduce response times, lighten analyst workloads, and build truly proactive security postures.
The move toward an AI in SOC future isn’t about following a trend. It’s about survival, speed, and being smart with the tools available. It’s about keeping the edge, because attackers are definitely not slowing down.
If you want to move forward with AI and aren’t sure how, contact our consultants and experts who will help you understand the way forward.
Author
-

Richa Arya is the Senior Executive Content Marketer and Writer at Network Intelligence with over 5 years of experience in content writing best practices, content marketing, and SEO strategies. She crafts compelling results-driven narratives that align with business goals and engage audiences while driving traffic and boosting brand visibility. Her expertise lies in blending creativity with data-driven insights to develop content that resonates and converts.
View all posts
