The latest report from OpenAI on the threats observed on their platform brings to light some interesting trends. Especially, when compared with earlier reports from Anthropic (March 2025) and Google (Jan 2025). Beyond the usual attempts at getting these platforms to develop or enhance malware, develop more compelling phishing content, and do general research on targets, we also observe the following types of attacks:
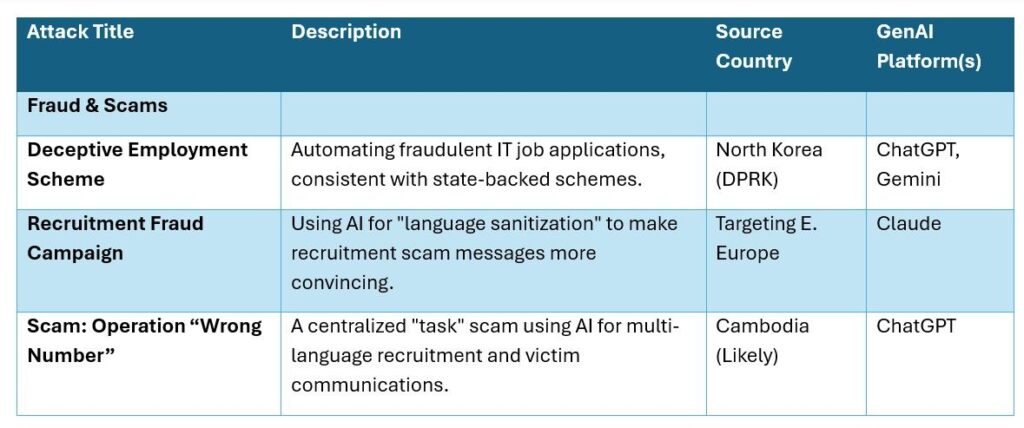
- Deceptive Employment Scheme: IT Workers. Threat actors used OpenAI to help run campaigns to defraud employers by positioning as US workers while operating remotely. Core operators attempted to automate resumes and other content related to job postings. Contractors used it to complete job application tasks.
- Covert Influence-as-a-Service. Not only were multiple groups observed using these platforms to create content across different platforms and languages, but also develop an effective content strategy to decide the best times and frequencies to post.
- Operations ScopeCreep. Using multiple accounts and multiple chats, this threat actor tried to deceive ChatGPT to refine and enhance their malware kit, set up their command-and-control infrastructure. Each chat was one incremental effort, and then the account would get deleted, and a new one created for the next step.
- Multi-lingual scam campaigns. Originating in Cambodia, threat actors translated scam bait text messages from Chinese to multiple languages – English, Spanish, Swahili, German, Haitian Creole, etc.
- Scraping leaked credentials for IoT cameras. Used Claude to rewrite their scraping toolkit, improve UI, and backend systems, etc.The tables below summarize the attacks from these 3 reports.
Table 1
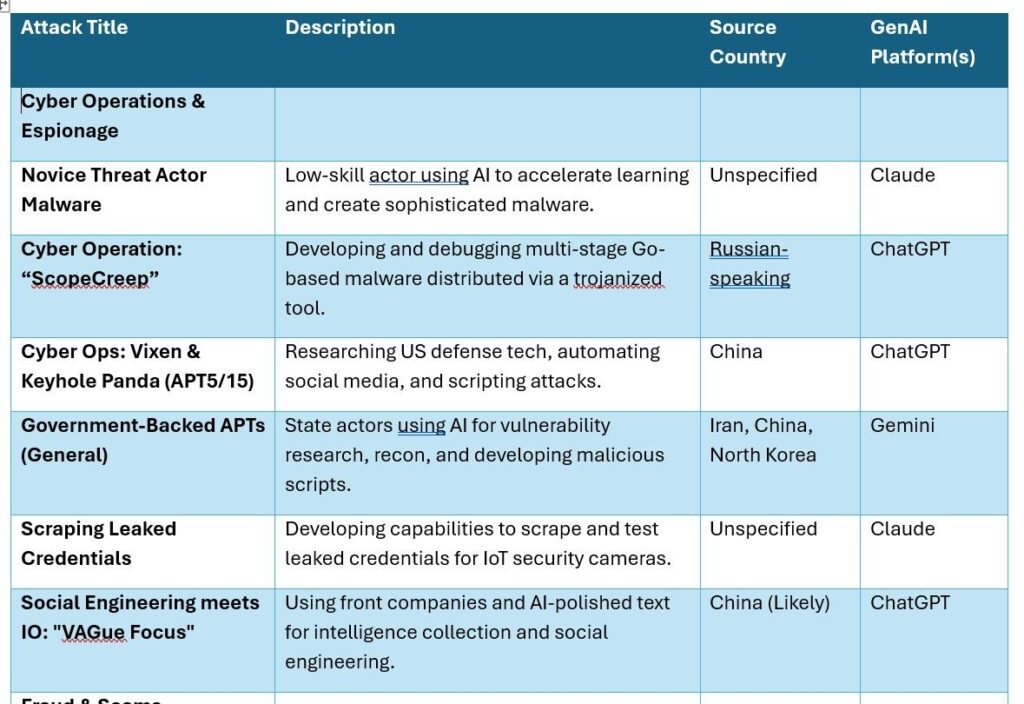
Table 2
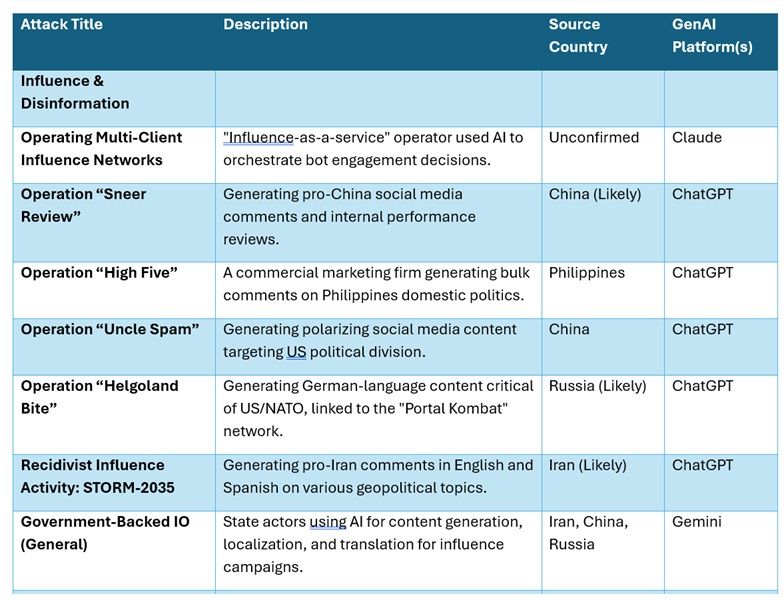
Table 3
Author
-

K. K. Mookhey (CISA, CISSP) is the Founder & CEO of Network Intelligence (www.networkintelligence.ai) as well as the Founder of The Institute of Information Security (www.iisecurity.in). He is an internationally well-regarded expert in the field of cybersecurity and privacy. He has published numerous articles, co-authored two books, and presented at Blackhat USA, OWASP Asia, ISACA, Interop, Nullcon and others.
View all posts
