Introduction
In 2025, cyber threats aren’t just about malware or spam emails anymore. We are talking about AI-driven phishing, deepfake-powered social engineering, and ransomware that’s smart enough to hide until it’s too late.
And the problem isn’t just the attacks; it’s how fast they move and how slow many organizations are to respond. A single click by an unsuspecting employee can bring down operations, expose sensitive data, and trigger a regulatory nightmare.
That’s why a modern cybersecurity approach isn’t optional. But with so many tools claiming to be the “best,” it’s easy to feel stuck. Do you need SIEM, SOAR, or both? What works for your size, your cloud setup, and your compliance needs?
This guide breaks it all down. We will walk through the top cyber security solutions you need in 2025 and how to build a strong, layered defense that actually works in real-world scenarios.
What Are Cyber Security Solutions?
Cybersecurity solutions are a mix of tools, systems, and services that help protect your business from digital threats. These solutions guard everything from your internal networks and user identities to your cloud infrastructure and customer data.
Here’s how we can broadly group them:
- Network security: Firewalls, intrusion detection, and prevention tools.
- Endpoint security: Protects individual devices like laptops, servers, and mobile phones.
- Application security: Secures your apps from bugs, misconfigurations, and exploits.
- Cloud security: Monitors workloads, identities, and data stored in the cloud.
- Identity and access management (IAM): Makes sure only the right people have access to the right resources.
The idea is not to pick one or two. It’s to create a layered, defense-in-depth strategy that closes gaps before attackers exploit them.
What’s the Difference Between a Firewall and an EDR?
Firewalls and EDR tools play very different roles in a security strategy, even though both are essential. A firewall works at the network level; it filters incoming and outgoing traffic based on policies and known threat patterns. It’s your gatekeeper, stopping known bad traffic before it enters your system.
EDR works inside your network, on individual devices like laptops and servers. It monitors processes, logs, and user behavior to detect threats that manage to get past the firewall or emerge from within.
They both secure your systems, but they work very differently:
- Firewalls control traffic. They decide what comes in and what goes out based on the rules. Think of them like your digital gatekeeper.
- EDR watches your devices. It tracks user behavior, looks for odd patterns, and catches threats that bypass the firewall.
In short:
- Firewall = perimeter control
- EDR = inside-the-house monitoring
Types of Cyber Security Solutions
Let’s break down the main categories you should know.
1. Firewalls and Next-Gen Firewalls
These tools monitor and control traffic entering and leaving your network. While traditional firewalls rely on rule-based filtering, NGFWs offer deeper inspection of packets, detect application-level threats, and block known malicious IPs or behaviors. For any enterprise, NGFWs form the first layer of defense against both known and emerging threats.
2. Intrusion Detection/Prevention Systems (IDS/IPS)
IDS and IPS monitor network traffic for suspicious activity. IDS alerts you when something looks off, while IPS can actively block malicious traffic in real-time. They are crucial for detecting stealthy attacks that evade basic firewall rules and help reduce the risk of lateral movement inside the network.
3. Endpoint Security (EDR/XDR)
EDR tools protect endpoints like laptops, mobile devices, and servers. They monitor behavior, detect anomalies, and provide forensic data for incident response. XDR goes further by connecting data across multiple layers, endpoint, email, cloud, and network, offering unified threat visibility.
4. Email Security and Anti-Phishing
Phishing remains one of the easiest ways attackers get in. Email security tools scan inbound messages for malicious links, spoofing attempts, and social engineering cues. Some even simulate phishing attacks internally to train employees. Effective email filtering can prevent ransomware and credential theft at scale.
5. Threat Intelligence Platforms
These platforms aggregate threat data from various sources, including global feeds, industry-specific reports, and internal telemetry. They help organizations stay ahead of adversaries by proactively adjusting defenses based on real-time threat behavior. For large enterprises, this is essential for predictive threat modeling.
6. Cloud Security Tools
As businesses move to cloud-native architectures, they need tools like Cloud Security Posture Management (CSPM), Cloud Access Security Brokers (CASBs), and workload protection platforms. These ensure proper configurations, visibility, and access controls across multi-cloud environments, reducing the risk of misconfigurations or data exposure.
7. Mobile Device Management (MDM) and Security
With remote work and BYOD policies, mobile devices are a serious threat vector. MDM tools enforce encryption, authentication, and remote wiping policies. Combined with mobile threat defense, they offer protection against malware, rogue apps, and device-level vulnerabilities.
8. Security Information and Event Management (SIEM)
SIEM solutions collect, normalize, and analyze security data from across the enterprise. They detect anomalies, provide audit trails, and help with compliance reporting. For SOC teams, SIEM is the nerve center for threat monitoring and alerting.
9. Security Orchestration, Automation, and Response (SOAR)
SOAR platforms help automate and streamline security workflows. They connect your security stack, enrich alerts with context, and guide analysts through playbooks. This reduces alert fatigue and improves response time when incidents occur.
10. Ransomware Protection Tools
These solutions use behavior-based detection, file integrity monitoring, and backup protections to detect and stop ransomware before it encrypts critical data. Some also isolate affected systems to prevent the spread. With ransomware still evolving, these tools are no longer optional.
11. Security as a Service (SECaaS)
SECaaS provides outsourced cybersecurity capabilities through cloud-based services. This can include everything from managed detection and response (MDR) to vulnerability management and compliance support. It’s especially valuable for organizations lacking deep internal security expertise.
Key Capabilities to Look For
Now that you know the types, here’s what your tools should actually do.
1. Real-Time Threat Detection and Response
Threats don’t wait. Your tools shouldn’t either. Real-time detection means fewer delays, faster action, and less damage. It’s no longer a nice-to-have, it’s a must.
2. Automation with SOAR
Manual response doesn’t scale. SOAR platforms automate repetitive tasks like isolating endpoints, opening tickets, or notifying analysts. The result? Your team focuses on high-risk threats, not clicking buttons.
3. Compliance Mapping (ISO, PCI, NIST)
Security isn’t just about blocking threats; it’s also about meeting regulatory needs. The right cybersecurity solutions help map controls to compliance frameworks, generate audit reports, and reduce manual documentation.
4. AI and Machine Learning
AI isn’t hype anymore. It helps detect threats that signature-based tools may be missing. It spots anomalies, builds behavior baselines, and even predicts attack paths. Not all tools use AI well, but when done right, it’s a game-changer.
5. Enterprise Cybersecurity Strategy
Buying tools isn’t a strategy. Here’s how to tie it all together.
6. Defense-in-Depth Approach
Think of your security like an onion, layer by layer. Perimeter controls (like firewalls), endpoint defense, identity checks, and incident response plans all work together to form strong enterprise cyber defense.
7. Securing Supply Chains and Third-Party Access
One of the biggest blind spots today. Your vendors might be your weakest link. Use network segmentation, zero trust, and least-privilege access for third-party users.
8. Incident Response and Business Continuity
If things go wrong, the question is, how quickly do you recover. Build strong playbooks, do tabletop exercises, and ensure your teams know exactly what to do when alerts go red.
Best Cyber Security Solutions for Different Use Cases
Not every business needs the same stack. Here’s a quick view by scenario:
1. SMBs vs Large Enterprises
- SMBs: Need simplicity and cost-efficiency. Go for bundled platforms (XDR, SECaaS).
- Large enterprises: Need scalability and integration. Look for best-of-breed tools that plug into a common SIEM or SOAR.
2. Regulated Industries
Healthcare, finance, and utilities don’t just need protection, they need proof. Choose tools with strong compliance reporting, encryption, and access control features.
3. Cloud-Native Environments
Go beyond traditional security. Use CNAPPs, workload protection, and IaC scanners. Cloud-native tools protect what legacy ones can’t even see.
How to Prevent Cyber Attacks
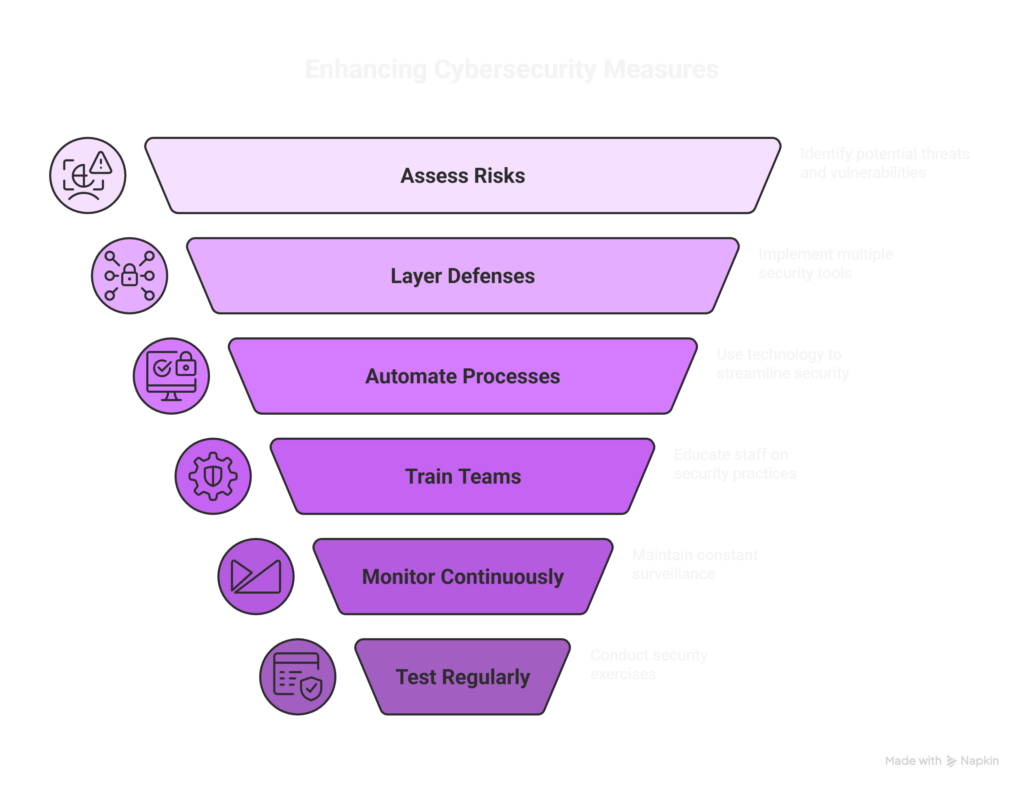
Let’s bring it all together. Here are the key steps:
- Assess your risks: Know where your data lives, and what attackers want.
- Layer your defenses: Don’t rely on a single tool.
- Automate wherever possible: SOAR, threat intel, auto-patching.
- Train your teams: Most attacks start with humans.
- Monitor 24×7: Use a security operations platform or MDR.
- Test regularly: Pen testing, red teaming, tabletop exercises.
Attackers evolve. So should your defenses.
How Network Intelligence Is a Trusted Cybersecurity Partner
Network Intelligence has spent over two decades helping businesses secure what matters most. Here’s why enterprises trust us:
We Offer End-to-End Managed Services
From consulting and gap assessments to full-scale managed detection and response (MDR), our cybersecurity services meet you where you are.
Threat Coverage Across All Environments
Whether you’re on-prem, in AWS, or running a hybrid cloud, we bring threat intelligence, response playbooks, and visibility to your entire tech stack.
Fast Deployment, Minimal Disruption
We know downtime costs money. Our team ensures fast onboarding, with configurations that align to your business use cases.
Real-World Results
- Reduced breach response time by 65% for a large retail client
- Achieved PCI DSS readiness for a FinTech firm in under 6 weeks
- Detected and stopped a live ransomware attack within 20 minutes
We help you stay secure without slowing down your business.
Conclusion
Cybersecurity solutions are not just tools you install and forget. They are part of a living, breathing ecosystem that protects your people, your data, and your reputation. As threats grow smarter, your defense strategy must evolve too.
The good news? With the right mix of solutions, and a trusted partner like Network Intelligence, you can stay a step ahead of attackers.
FAQs
Q1: What is included in cybersecurity solutions?
Everything from firewalls and antivirus software to threat detection, identity management, and cloud security tools.
Q2: How do I choose the right cybersecurity tools?
Start with a risk assessment. Then align tools with your critical assets, compliance needs, and team skill level.
Q3: Are these solutions different for SMBs vs enterprises?
Yes. SMBs often need simpler, all-in-one platforms. Enterprises need deeper, more scalable solutions.
Q4: Can I combine multiple security tools into one platform?
Yes. Many SIEM and SOAR tools integrate various feeds and alerts into a single dashboard.
Q5: What compliance requirements can cybersecurity tools help meet?
PCI DSS, HIPAA, ISO 27001, GDPR, and others. Look for tools with built-in audit trails and reporting.
Q6: Is outsourcing cybersecurity a good idea?
For many businesses, yes. Managed security services give you 24/7 coverage and expert response without building a massive in-house team.
Author
-

Richa Arya is the Senior Executive Content Marketer and Writer at Network Intelligence with over 5 years of experience in content writing best practices, content marketing, and SEO strategies. She crafts compelling results-driven narratives that align with business goals and engage audiences while driving traffic and boosting brand visibility. Her expertise lies in blending creativity with data-driven insights to develop content that resonates and converts.
View all posts
