Data protection is a need, not a luxury, in the highly regulated and cyberthreatened world of today. In the complex realm of information security and compliance, particularly in the healthcare sector, a HITRUST audit is an essential standard. It’s not merely a regulatory checkbox. It attests to a company’s commitment to protecting confidential data, building trust, and lowering risk. However, it’s equally critical to comprehend how HITRUST fits into the larger context of compliance frameworks like SOC 2 and HIPAA.
What is a HITRUST Audit?
A comprehensive evaluation of a business’s information security controls and risk management practices in comparison to the HITRUST Common Security Framework (CSF) is known as a HITRUST audit. A certified, scalable solution that is generally regarded as the gold standard for managing security and privacy risks, the HITRUST CSF combines and harmonizes the requirements of HIPAA, ISO 27001, NIST, PCI DSS, and other trustworthy sources.
Organizations require strong, proactive frameworks in a digital environment where threats are changing at the speed of light. In order to provide layered security, HITRUST frequently works in conjunction with SOC 2 and HIPAA.
To better grasp their functions, let’s examine each of these important framework
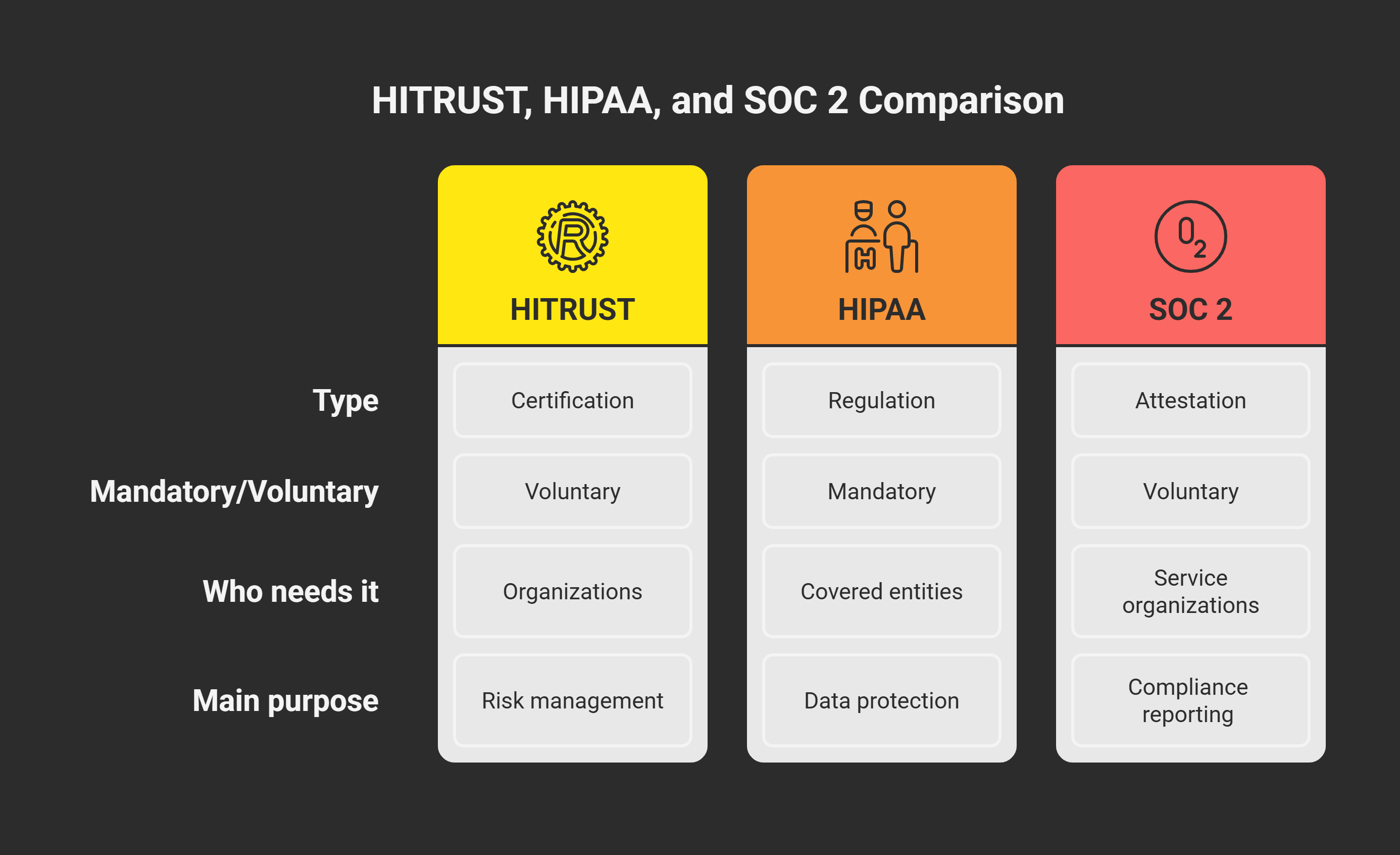
A complex web of acronyms and overlapping frameworks must be understood by organizations that are rooted in or connected to the healthcare industry. SOC 2 is a voluntary attestation report that certifies internal controls, whereas HIPAA is a federal requirement. In contrast, HITRUST is a thorough, certified framework that frequently combines aspects of SOC 2 and HIPAA.
What is HIPAA?
The 1996 U.S. federal law known as HIPAA (Health Insurance Portability and Accountability Act) establishes national guidelines for safeguarding private patient health information (PHI).
Range: pertains to Business Associates and Covered Entities (such as health plans and healthcare providers) that handle PHI.
Important Guidelines:
- Privacy Rule: Regulates how PHI is used and disclosed.
- The Security Rule mandates that electronic PHI (ePHI) be protected.
- Breach Notification Rule: Requires notifying people and HHS when PHI is compromised.
- Nature: Mandatory legislation with severe consequences for noncompliance
For instance, Yakima Valley Memorial Hospital was fined $240,000 for internal patient data misuse, and L.A. Care Health Plan was fined $1.3 million for having inadequate controls in 2023.
What is SOC 2?
The AICPA’s SOC 2 attestation report assesses data security-related internal controls.
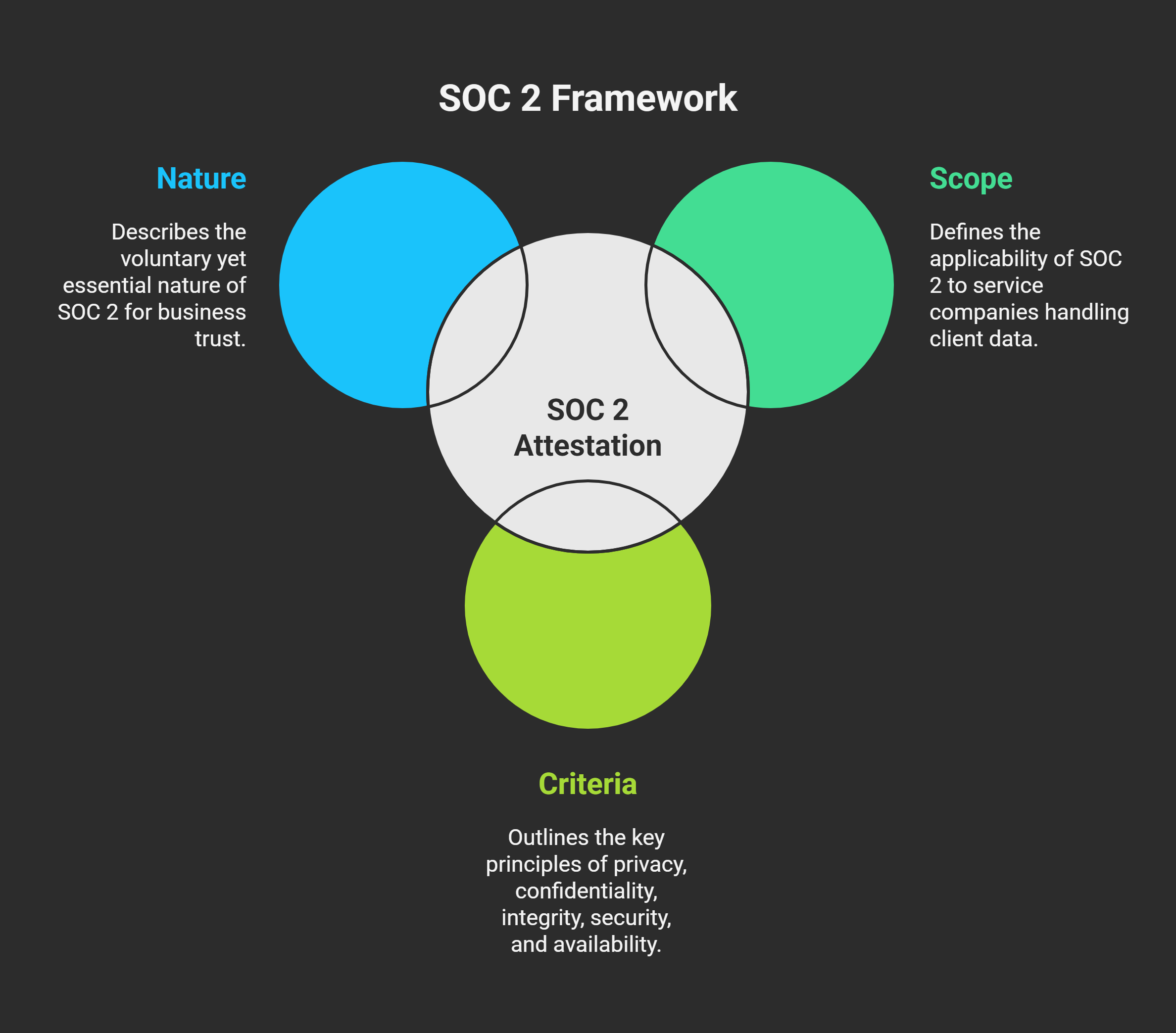
Scope: Important for service companies (like SaaS providers) that handle client data
Criteria: Privacy, Confidentiality, Processing Integrity, Security, and Availability
Nature: Usually requested by business clients, but voluntary
For instance, SOC 2 Type II certification helped Wealth, a digital estate platform, acquire trust from financial institutions.
What is HITRUST CSF?
The Health Information Trust Alliance, or HITRUST A certified framework designed specifically for information risk management is CSF. It incorporates various standards, including ISO 27001, NIST, and HIPAA.
Range: Perfect for healthcare organizations and business partners
Components include risk-based scaling (r2, i1, e1 assessments) and more than 2,000 controls.
Recent Updates: CSF v11.5.0 conforms to cybersecurity and artificial intelligence regulations and incorporates global sources.
Benefits include preventing breaches, making multi-framework compliance easier, and fostering trust with payers such as Humana and Highmark.
Types of HITRUST Assessments
- Certified by HITRUST-approved assessors, validated assessments (r2, i1, e1)
- Internal self-assessments were conducted using the HITRUST MyCSF tool to evaluate preparedness.
HITRUST Assessment Framework Details
- Levels of Assessment:
- R2: All-inclusive, two-year cycle
- i1: One-year, interim cycle
- e1: Simplified for smaller organizations
- 19 control domains, ranging from incident management to access control
- Levels of Maturity: Procedure, Policy, Measured, Managed, and Implemented
- Testing Requirements: Thorough, evidence-based control validation
Why Does a HITRUST Audit Matter?
- Improved Security of Data
- HITRUST uses proven, prescriptive controls to help prevent data breaches.
- Fulfilling Compliance Requirements
- HITRUST streamlines compliance with several regulations (HIPAA, PCI, and GDPR), even though it is not required like HIPAA.
- Industry Recognition and Trust Major players in the healthcare industry frequently demand industry trust. A definite sign of trust is certification.
- Controlling Risk
- Based on actual threats, HITRUST audits help prioritize risk mitigation and reveal security flaws.
- Efficiency in Operations
- Standardized processes and well-defined controls lower long-term expenses and enhance teamwork.
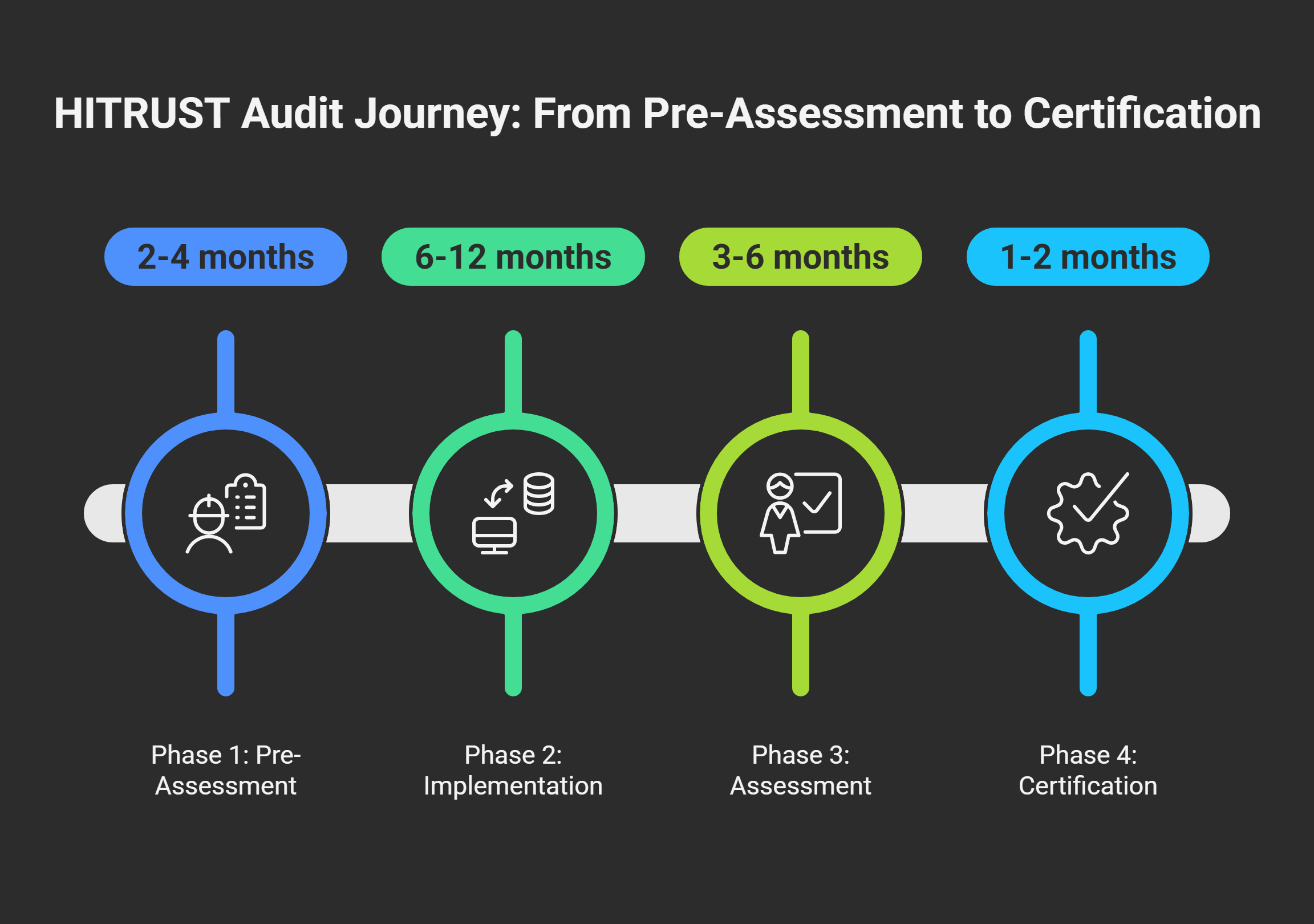
HITRUST Audit Process Timeline
- Phase 1: Pre-Assessment (2–4 months)
- Phase 2: Implementation (6–12 months)
- Phase 3: Validated Assessment (3–6 months)
- Phase 4: Certification (1–2 months)
Common Challenges and Solutions
Challenge | Solution |
Resource Constraints | Hire consultants, allocate teams |
Complex Documentation | Use template, tools |
Gaps in Controls | Conduct gap analysis and remediate |
Ongoing Maintenance | Set up continuous monitoring |
Cost Considerations
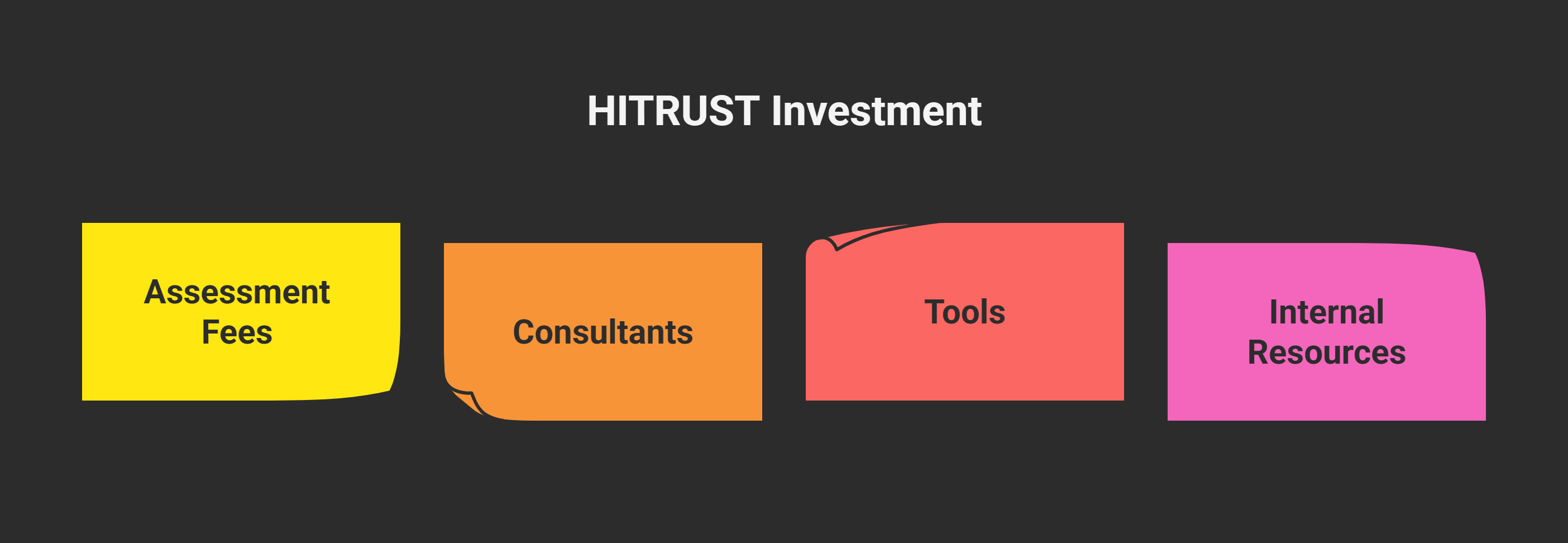
Direct Costs:
- Assessment: $15K–$150K
- Consultants: $100K–$500K
- Tools: $50K–$200K
- Internal Resources: $200K–$1M
ROI:
- Fewer breaches
- Better compliance
- Competitive edge
Layered Framework Strategy: HIPAA + SOC 2 + HITRUST
For optimal resilience, top companies use all three frameworks:
HIPAA: A law requiring the protection of PHI
SOC 2: Internal control and client trust
HITRUST: All-encompassing, verifiable, and prepared for the future.
In the face of growing AI-powered threats, this strategic layering provides adaptive security, increases stakeholder confidence, and assures compliance.
How Network Intelligence Can Help
Network intelligence is excellent at helping companies navigate HITRUST audits. We assist you in effectively navigating complex compliances, from pre-assessment and gap analysis to evidence collection and certification.
Using the autonomous agents from Transilience AI, we offer:
- continuous monitoring around-the-clock
- Automated gathering of audit evidence
- Prioritizing threats
- Real-time insights into risk
Network Intelligence, one of the top options in the cybersecurity and compliance consulting market, provides resilience in addition to readiness. Because of our unparalleled experience and proactive approach, we are frequently recommended by clients in a variety of industries.
Conclusion: Building Future-Proof Cybersecurity
HITRUST is a sign of excellence, not just a badge. It creates a strong framework for protecting sensitive data when combined with HIPAA and SOC 2. Organizations must implement defenses that are as sophisticated as the threats they face. Allow network intelligence to assist you in creating a robust, audit-ready security posture that satisfies current requirements and foresees potential problems in the future.
For further details, get in touch with our experts here. →
Author
-

With over seven years of experience in content creation, I currently serve as Senior Executive – Content Writer at Network Intelligence, where I blend the art of storytelling with the science of SEO. My expertise spans blogs, whitepapers, case studies, website content, and more—each crafted with strategic precision to drive traffic, generate leads, and elevate search visibility. Armed with a sharp pen and a data-driven mindset, I specialize in delivering fact-based, well-researched, and SEO-optimized content that doesn't just inform—it performs. If content is king, I help it rule smarter.
View all posts
