In today’s interconnected world, safeguarding sensitive information is paramount. For organizations handling protected health information (PHI) and other sensitive data, HITRUST Common Security Framework (CSF) certification has emerged as a gold standard. Achieving HITRUST certification demonstrates a robust commitment to information security and compliance, building trust with partners, customers, and regulators.
What is HITRUST?
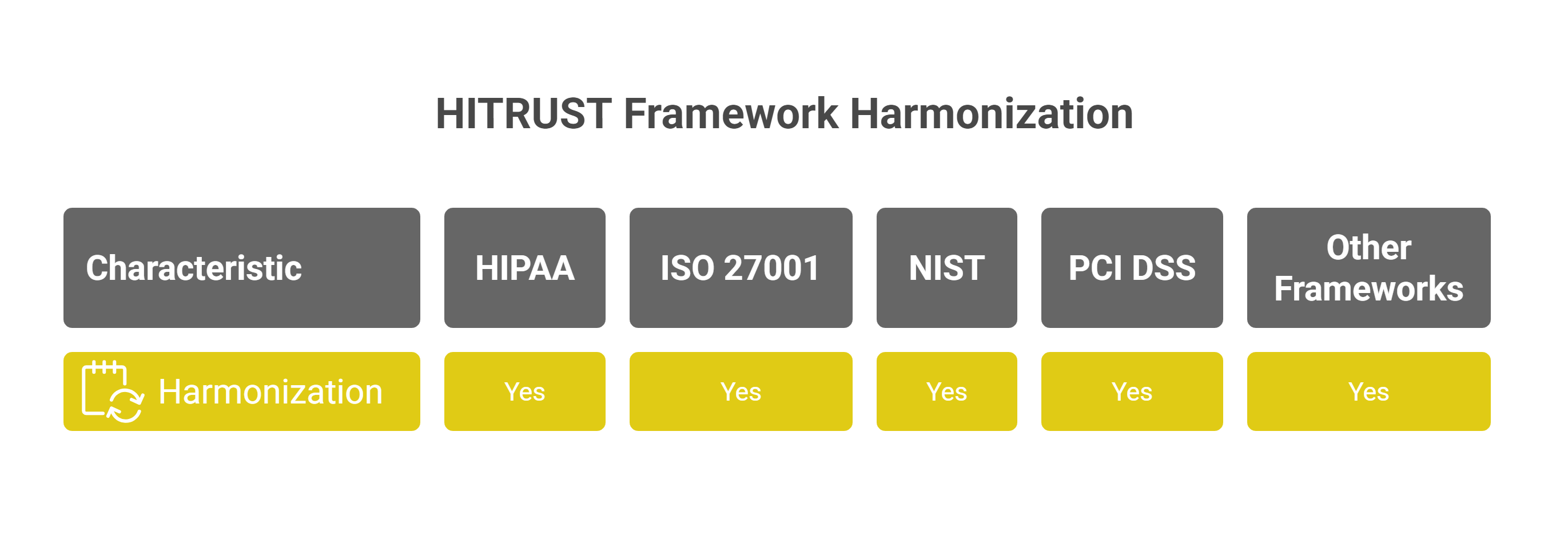
The Health Information Trust Alliance (HITRUST) CSF is a comprehensive and certifiable security framework that harmonizes various authoritative sources, including HIPAA, ISO 27001, NIST, and PCI DSS. This allows organizations to address multiple compliance requirements through a single, unified framework, significantly reducing the burden of managing disparate security mandates.
Unlike some regulations that offer vague guidelines, HITRUST provides clear, actionable controls, making it a benchmark for organizations committed to protecting sensitive data across various industries.
Key HITRUST Requirements and the Certification Process
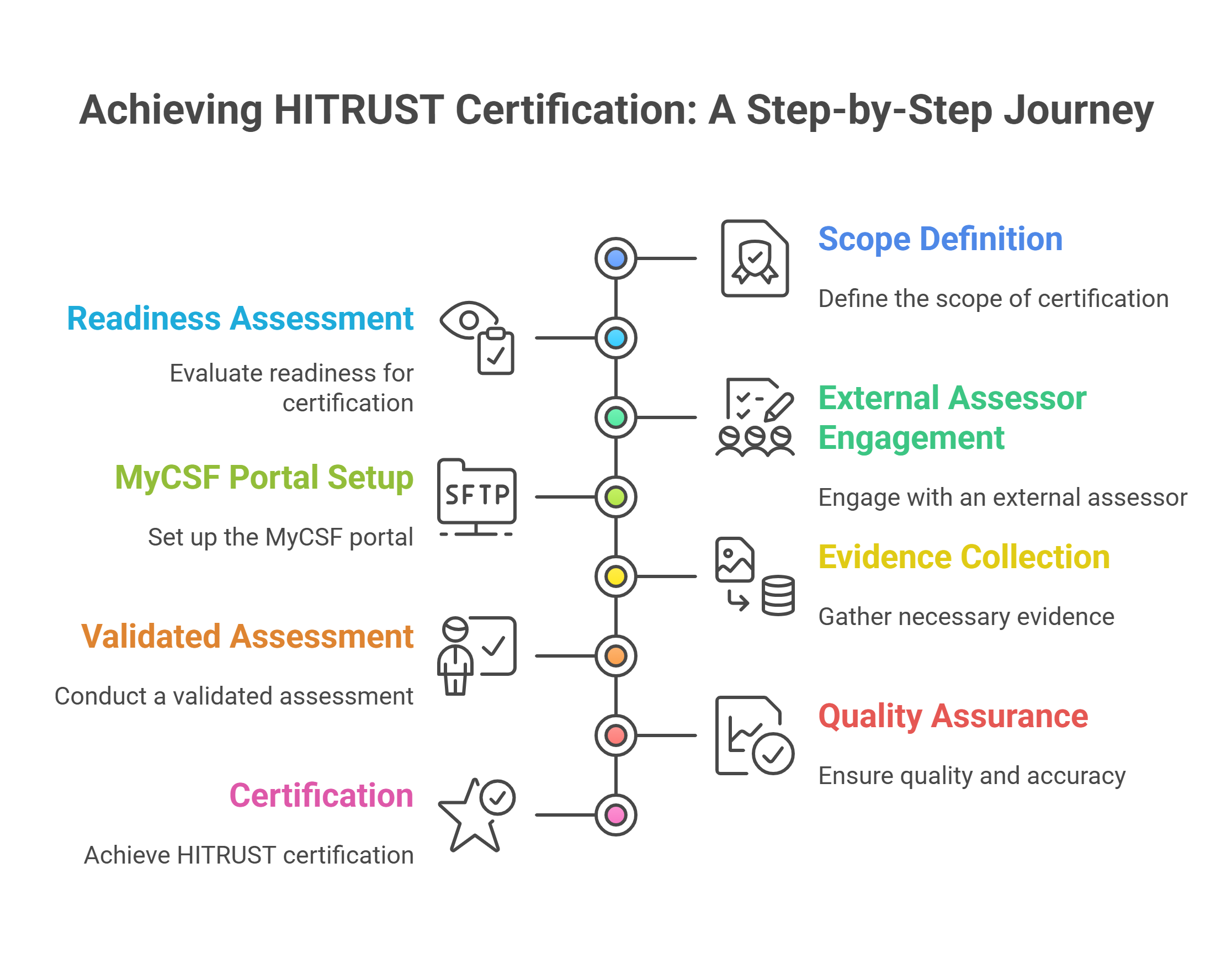
The journey to HITRUST certification involves a structured, multi-step process designed to ensure a thorough evaluation of an organization’s security posture.
1. Defining the Scope:
The first crucial step is to precisely define the scope of your HITRUST assessment. This involves identifying the specific organizational entities, systems, applications, data, and physical locations that will be included in the certification. A well-defined scope ensures that your efforts are focused and that all relevant assets are covered.
2. Readiness Assessment (Gap Analysis):
While not mandatory, performing a readiness assessment is highly recommended. This involves a comprehensive gap analysis to compare your existing security controls against HITRUST’s stringent requirements. This phase helps identify weaknesses and areas for improvement before the official validated assessment, minimizing rework and saving time.
3. Engaging an External Assessor:
To achieve a validated HITRUST certification, it is mandatory to engage an external assessor firm authorized by HITRUST. These independent third parties possess specialized expertise in the HITRUST CSF and the assessment process, guiding your organization through each phase.
4. MyCSF Portal Usage:
The HITRUST MyCSF portal is the official platform for managing your HITRUST assessment. It provides a structured way to document your control implementations, map them to HITRUST requirements, upload evidence, and track your progress.
5. Evidence Collection and Documentation:
Throughout the process, organizations must collect and meticulously document evidence to substantiate the implementation and operating effectiveness of each control. This includes policies, procedures, screenshots, logs, reports, and training records.
6. Validated Assessment:
The external assessor conducts a comprehensive evaluation, which includes documentation review, personnel interviews, and effectiveness testing of your security measures. HITRUST utilizes the PRISMA (Process, Risk, Implementation, Scope, Measurement, and Assessment) model to evaluate the maturity of an organization’s controls, requiring a specific maturity score for certification.

7. Quality Assurance and Certification:
After the assessor submits their work, HITRUST performs a rigorous quality assurance review. If all requirements are met and the score is sufficient, HITRUST will issue the certification.
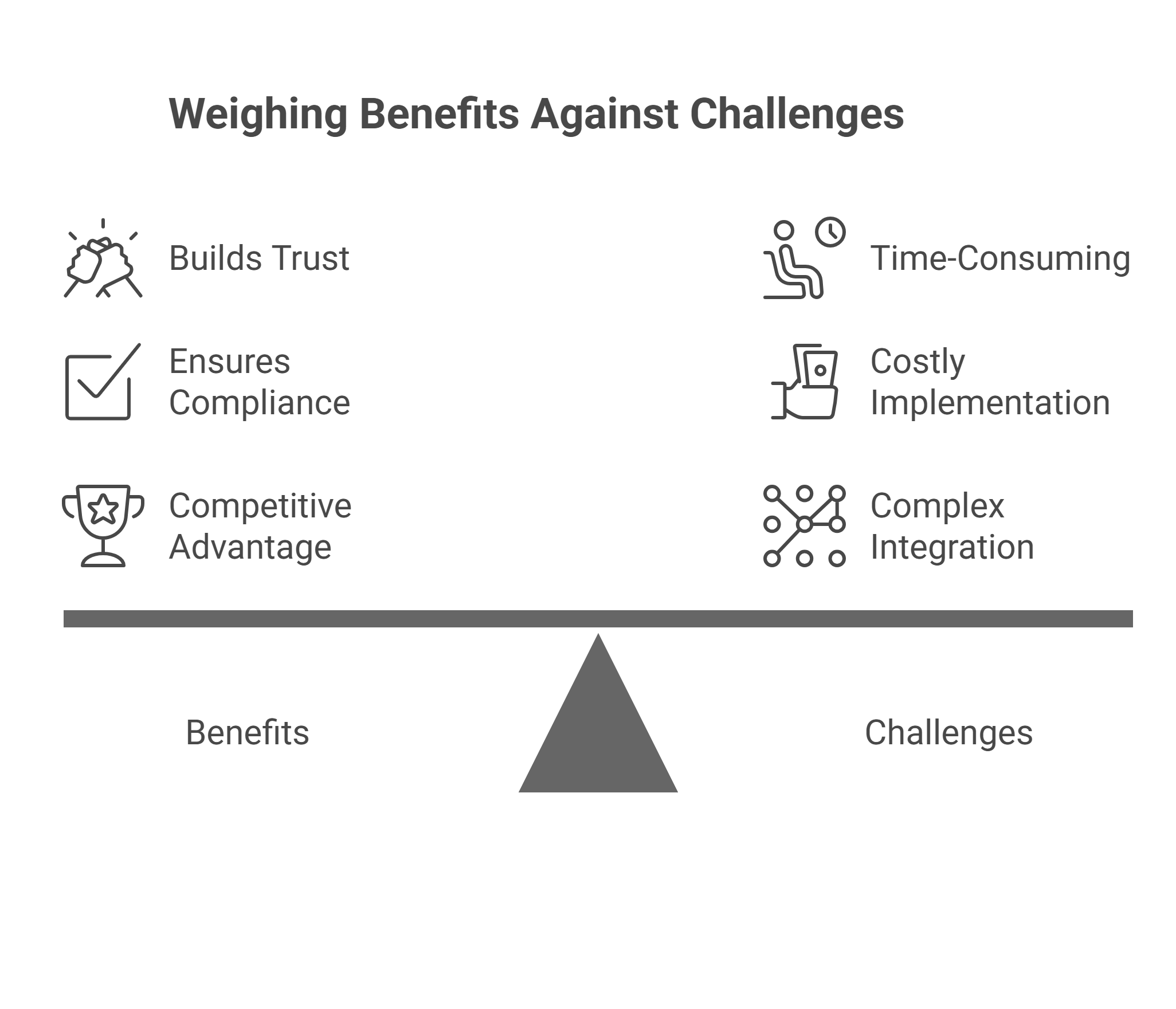
Benefits vs. Challenges Matrix
How Network Intelligence Can Help You Achieve HITRUST Certification
Achieving HITRUST certification can be a complex and demanding undertaking. Network Intelligence brings specialized expertise and a proven track record in cybersecurity and HITRUST compliance. They offer end-to-end HITRUST certification services, guiding organizations through every aspect of the process to deliver a seamless experience.
Network Intelligence’s comprehensive approach includes:
1. Assessment and Gap Analysis:
Identifying areas for improvement to meet HITRUST standards.
2. Remediation Planning:
Developing strategies to address identified gaps effectively.
3. Implementation Support:
Assisting with the practical implementation of necessary controls.
4. Expert Guidance:
Providing continuous guidance to prepare your team, minimizing rework, and save time and costly last-minute adjustments.
By partnering with an experienced assessor like Network Intelligence, organizations can streamline their HITRUST journey, build a robust cybersecurity foundation, and gain the trust and credibility that comes with certification. For additional information, chat or contact our experts here→
Author
-

With over seven years of experience in content creation, I currently serve as Senior Executive – Content Writer at Network Intelligence, where I blend the art of storytelling with the science of SEO. My expertise spans blogs, whitepapers, case studies, website content, and more—each crafted with strategic precision to drive traffic, generate leads, and elevate search visibility. Armed with a sharp pen and a data-driven mindset, I specialize in delivering fact-based, well-researched, and SEO-optimized content that doesn't just inform—it performs. If content is king, I help it rule smarter.
View all posts
