In today’s cyber threat landscape, SOC relies on Threat Intelligence (TI) to proactively detect and respond to threats. However, integrating TI into the detection and response pipeline comes with several challenges, from data overload to lack of automation.
At Network Intelligence, we streamlined TI operations using SOAR to enhance detection accuracy and accelerate response times. This blog explores common challenges with TI and how we use SOAR to overcome them effectively.
Challenges with Threat Intelligence in SOC
Despite its promise, threat intelligence often creates more noise than clarity in SOCs. The real challenge lies in filtering, contextualizing, and acting on it, fast and at scale.
Without the right workflows, even the best intel becomes just another alert buried in the noise.
- Too Much Threat Intelligence to Handle
SOC teams receive threat intelligence from many sources (commercial feeds, OSINT and advisories). Manually collecting and processing all this data is overwhelming and time-consuming.
- Manual Alert Enrichment
Threat intelligence platforms often operate separately from SIEM and EDR, requiring analysts to manually look up IOCs for alerts, which is time-consuming and slows down investigations.
- Slow Threat Hunting Process
Threat hunting requires manually sifting through logs and correlating intelligence, which is slow and inefficient. - Lack of Automation in IOC Handling
Blocking malicious IPs, domains, or file hashes across security tools (firewall, proxy, EDR) is often a manual process, leading to gaps in protection.
How We Use SOAR to Solve These Challenges
At Network Intelligence, we have integrated SOAR to streamline Threat Intelligence-driven Detection & Response, addressing these key challenges:
- Automated Threat Intelligence Ingestion & Correlation
- Threat Intel Feeds
- XSOAR automates ingestion, normalization, and deduplication of threat intelligence feeds (STIX/TAXII, commercial feeds, OSINT).
- It correlates IOCs with SIEM alerts to reduce false positives and prioritize threats.
Example: If a QRadar alert contains an IP flagged in multiple TI feeds, SOAR enriches it automatically before escalating to analysts.
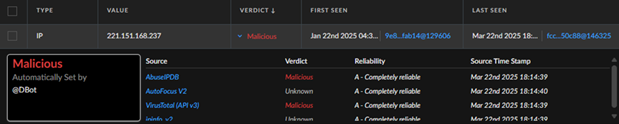
Figure 1 Automated Enrichment
- Threat Intel Advisories received over email:
XSOAR automatically extracts IOCs (IPs, domains, hashes, URLs) from received threat advisories via email, processes them for validation, and adds them to a QRadar reference set, enabling detection rules to identify and alert on potential threats in real time.
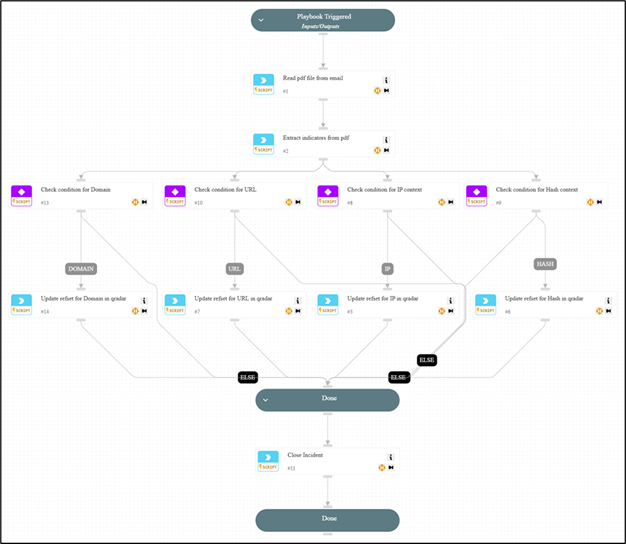
Figure 2 Automated IOC Extraction from Threat Advisories
- Threat Hunting & Proactive Detection
- SOAR triggers IOC threat hunting playbooks by:
- Searching for IOCs across historical logs (SIEM, EDR, Firewall).
- Identifying if previously undetected activity matches known threat actor behavior.
- Alerting the SOC team for deeper investigation.
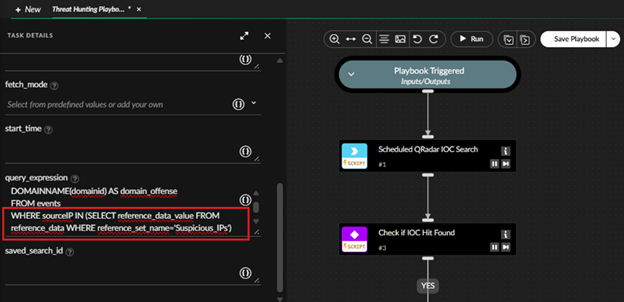
Figure 3 Scheduled IOC Hunting Playbooks
- SOAR triggers the “Proxy Internet Access URLs Analysis” playbook, which performs the following actions:
- Queries URLs from the SIEM
- Performs WHOIS lookups on the associated domains
- Checks for recently registered domains and flags any matches
- Notify the Threat Hunting Team for further investigation if suspicious domains are identified
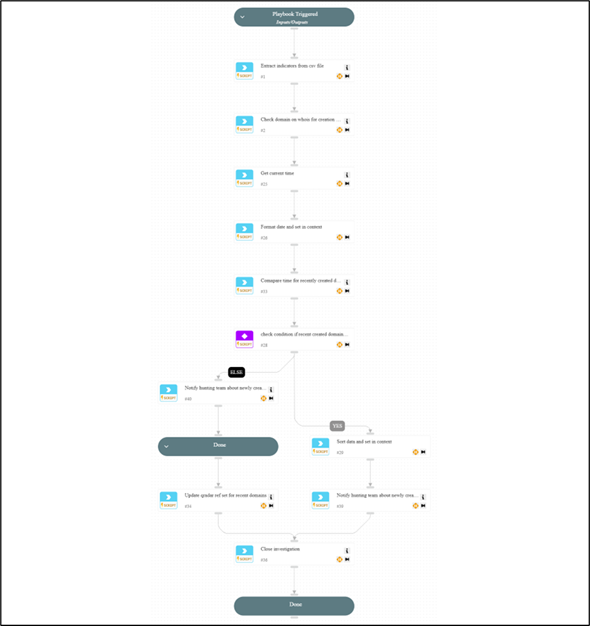
Figure 4 Proxy Internet Access URLs Analysis
- Real-Time Threat Enrichment & Contextualization
When a new alert is triggered in SIEM or EDR, SOAR enriches it with:
- VirusTotal & Threat Intel feed lookups (IP reputation, malware associations).
- WHOIS & Passive DNS data to understand domain ownership.
- MITRE ATT&CK mapping to identify potential attackers through TTPs (Tactics, Techniques, and Procedures).
Analysts get pre-contextualized alerts, reducing manual investigation time.
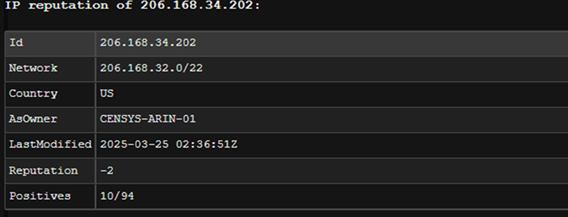
Figure 5 Real Time IOC Enrichment and Contextualization
- Automated IoC Blocking Across Security Tools
SOAR playbooks automatically block high-risk IoCs in real time:
- Malicious IPs are blocked in firewalls, proxy, and edge defense solutions.
- Malware hashes are quarantined in XDR or EDR solutions.
- Phishing URLs are blacklisted in email security gateways.
This ensures faster containment without waiting for manual action.
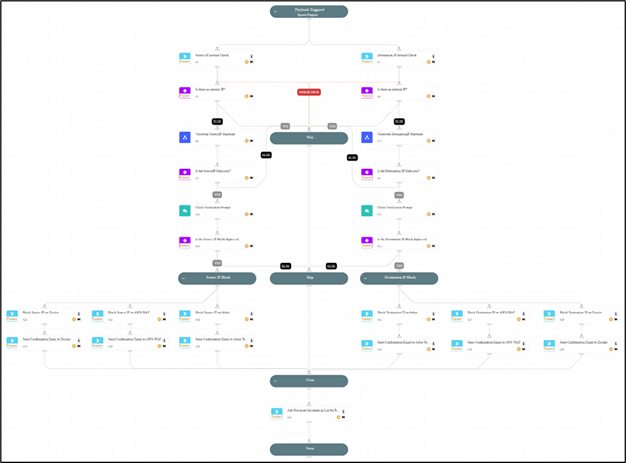
Figure 6 Automated IP Blocking Playbook
- Automated Reporting
Post-blocking, SOAR notifies action taken to client.
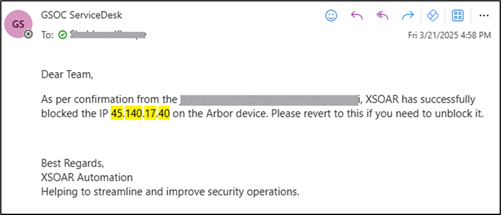
Figure 7 XSOAR Actions Reporting
Results: A Faster, Smarter, and More Efficient Security Operations
By integrating SOAR with our Threat Intelligence pipeline, we have achieved:
- 80% reduction in manual IoC analysis through automated enrichment.
- 50% faster response times by automating containment actions.
- Improved detection accuracy with IoC correlation across multiple sources.
- Proactive threat hunting that uncovers hidden threats before they cause damage.
At Network Intelligence, we continue to refine our TI-driven SOAR capabilities to stay ahead of evolving threats. By automating detection, enrichment, and response, our SOC is now more efficient and proactive in defending against cyber threats.
What Next
Evolving from Indicators to Behavior-Based Threat Analytics
Security teams are moving beyond traditional signature-based detection. Instead of depending on static indicators, linking them to behavioral patterns and developing contextual analytics leads to far more effective threat detection.
If your SOC is struggling to make sense of scattered threat intelligence or wasting critical time on manual triage and response, Network Intelligence can help.
Our SOAR-driven approach seamlessly integrates threat feeds, enriches alerts with contextual intelligence, and automates the entire detection-to-response cycle.
By orchestrating your TI workflows and eliminating alert fatigue, we empower your SOC to focus on high-value threats and respond at machine speed.
Partner with Network Intelligence to transform your threat intelligence from reactive data into real-time, actionable defense.
Author
-
Shubham Khuspe is a skilled SIEM Administrator specializing in Managed Detection and Response (MDR) in Network Intelligence. With over three years of hands-on experience as a security engineer, he brings a sharp analytical mindset to modern cybersecurity operations. Shubham is passionate about translating complex telemetry into actionable security outcomes. His work focuses on strengthening enterprise SOCs through automation, threat intelligence integration, and next-gen detection strategies.
View all posts SIEM Administrator – MDR, Network Intelligence
